On Monday morning, I got a call from one of our Executives telling me that his home computer was displaying a strange message and asking for some assistance. I asked what was displaying on the screen and he responded, “It’s asking for me to pay them money to get my files”. After listening to Steve Gibson’s (@SGgrc) and Leo Laporte’s (@leolaporte) Security Now podcast from last Wednesday (#427: A Newsy Week), I dreaded the answer to my next question. “Please read me what it says on the screen, ” I asked. He responded with, “Your personal files are encrypted! Your important files encryption produced on this computer…”, oh no…
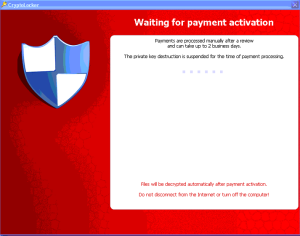
My Executive’s personal home computer had been infected with Cryptolocker. This is what the screen looked like (pardon the poor quality, these are camera phone shots):
I knew what I was facing because of Steve’s excellent description of the problem. I also knew we probably needed to pay the ransom to get my Executive’s personal files restored. However, I wanted to get more information about protecting our Enterprise, as well as more information on how the decryption and payment operated. So, off to Google…
I found a really good and thorough discussion of the Cryptolocker infection on BleepingComputer.com, They do a great job breaking down a lot of the information and providing some resources for Enterprises to combat the virus. They also have a VERY active support forum with over 85 pages of updates including over 1200 posts dating back to September 6, 2013.
So, I absorbed a lot of that information and set my team to work. I also sent someone over to my Executive’s home to work with him on recovery. The rest of this post is what we’ve done and our plans for the future.
Each computer’s infection has a Command / Control server that holds the public (and private) keys that were used to transmit the actual encryption key used to encrypt your files. This server’s operation is critical to the successful recovery of your personal (or business) files. So if it goes offline (or is taken offline) before you can pay the ransom, the key is lost. If you try to work around the infection, you risk the client telling the server to delete the key.
The Command / Control server is one of many that the software uses, the one for this infection was “http://eyebjjtyvkaulgh.org” and is presented on an information screen by the infection. Knowing that the Malware could get removed by anti-malware software, they provide a download link to the De(en)cryption software, so you can reinstall it. Nice! You’ll also notice the file icon which is a link to a file stored on your local hard drive that lists all of the files that were encrypted.
I decided to look up some information about that URL:
- According to DNS, the host resolves to the IP address 50.116.8.191
- According to WHOIS, the domain was registered with a Private Registration (no surprise) in Queensland, AU on October 26, 2013
- According to WHOIS, the DNS servers for the domain are: (ns1.happilyresist.com and ns2.happilyresist.com), most likely just the hosting providers stock servers.
- According to ARIN, the IP address is owned by Linode, a Virtual Server hosting provider located in Galloway, NJ
Based on the date of the registration, I suspect the domain was registered specifically for this infection, as that timing is suspiciously close to the date of the actual infection. If I’m right, that means that each infection has it’s own Command/Control server dedicated to it. The reason for the ransom countdown is that they only want to pay for the Command/Control server for a short time, and then they delete the entire server instance when the time expires, not just the key.
This is the HTML of our Command / Control Server, you can use some of the more unique strings found on this page to search Google for these servers, there is at least one other I found that is currently online. Also, note that the text and the background colors are the same. You have to highlight the page to see the text:
| 1 2 3 4 5 6 7 8 9 10 11 12 13 | "color: #0F0; background-color: #0F0;font-size:10%">
#
Temporary notes: 1. ****You cannot restore files after time has expired! Setting the system clock back will not help you! Uninstall action and expiry time controlled by server, your key pair destroyed after uninstall (time has expired)! You can't control it!!! After uninstall (if you try reinstall) you obtain a new key pair from server. You can reinstall software only if time has not expired! Uninstall temporary disabled. Soon will be available the decryption service... Stay with us 🙂 |
The Bitcoin address for the payment was 1AXgfzpiimunqsrSFn2qgM8YgKGqqgPwU4 (hasn’t been used, as it was most likely uniquely created just for this infection). We ended up purchasing a “Green Dot MoneyPak” and submitting it for payment of our ransom.
The infection provides lots of helpful instructions on how to buy and use a MoneyPak. It provided similar instructions on “Getting Started with Bitcoin” and how to make the payment. All very educational! Once payment was made, the following screen appeared:
At this time, you are awaiting the payment to be accepted and, hopefully, the decryption to begin. According to the screen the payment confirmation is a manual process and could take up to 2 days to process. Then of course, the decryption itself is going to take a while.
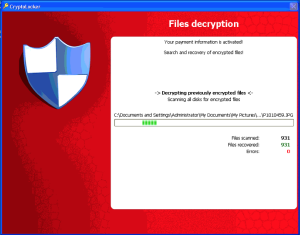
After waiting for approximately 2-3 hours, our payment was processed and the system automatically started decrypting files. It provides a window showing you what directory it’s working in and a list of the files that have been scanned and “recovered”.
Also, there is now a file on your Desktop called “Your Private Key.bin”, which is presumably the encryption key. I took a look at the file, but it’s a binary key, so not terribly useful. We archived a copy of it just in case.
Oddly, when scanning system directories (like “Program Files”) the “Files recovered” doesn’t increase, but the “Files scanned” does. The implication is that it’s scanning the entire drive again. Why? I’m not sure. We know the virus has a list of all of the files it encrypted, there shouldn’t be a reason to re-scan the whole drive(s), just decrypt all of the files in the list it already made.
At this point, I’m a bit nervous about the outcome. I’ve read where after decryption ends, the system BSODs, or reboots. If you let it reboot, it re-infects your system and you’re back to Square 1. However, I know for a fact that the decryption is happening because documents on the Desktop that were encrypted (and the icons changed because the file extension changed) are back to normal.
During the course of the decryption, we did log a few errors (3 I believe), these appeared to be Microsoft Office temporary files (autorecovery files actually), and I believe the tilde (~) in the file name is what caused the decryption to fail. The tilde is a special path character in Linux/Unix, and perhaps the decryption library doesn’t handle them correctly (although they appeared to encrypt fine!).
The decryption finally finishes and you’re presented with this screen:
At this point we have no idea what the software is doing. If you click Cancel we’re unsure what the software will do (it says it will delete itself), of course, for all we know the software is re-encrypting the whole drive as the system is sitting there. We opted to power off the system without interacting with the software at all. This seemed to be the best solution. We then pulled the drive from the system and are mounting it to an off-net (non-Windows) computer for file recovery.
I’ll post progress updates as we have them.
Why are these people doing this? Because crime does pay. The two Bitcoin addresses that were originally used in the early versions of the infection (back in September) were:
- 1KP72fBmh3XBRfuJDMn53APaqM6iMRspCh (Ransom payments recorded from September 7th through September 30)
- 18iEz617DoDp8CNQUyyrjCcC7XCGDf5SVb (Ransom payments recorded from October 1st through October 21st)
The two addresses above amassed 46 and 55 BTC respectively according to BlockChain.info. That’s 101 BTC in under 60 days, or $21,000 at today’s value. This of course only covers the two known addresses, there are hundreds (or thousands) more. By reading the BlockChain you could explore the addresses that were used to offload the coins out of those addresses, but that is tedious work.
As the great W.O.P.R. once said, “The only winning move is not to play.”:
- Don’t click links or open attachments inside email.
- Have a “Cold” backup in your home (i.e. not connected to your computer other than when it’s used to backup)
- Have an “Online” backup that is cloud-based and inaccessible to your computer as a volume (Carbonite or CrashPlan)
- Yes, if your files are important, you should have at least 2 backups.
Update – 20131029:
I can confirm that we have been able to recover all of the files by following the above procedure. We have opened a representative sample of different file types and they all open fine. Following the power-off of the system in question while it was at the “Retry/Cancel” screen (after decryption completed), we pulled the drive and attached it to a non-windows, non-networked Live booted computer. We then copied the files to another external drive and ran anti-virus and anti-malware (nothing found). We then moved the files to a USB stick and are in the process of building a new system. The original hard drive remains untouched other than the original copy of the personal files off of the drive. I suspect the virus is still resident on the drive (as we did not allow it to “delete the software from this computer”).
Update – 20131030:
A friend of mine over at aucontrary.com pointed out that something like Cryptolocker is very akin to the Daemon in the book Daemon by Daniel Suarez, also a favorite of Steve Gibson and Leo Laporte (Freedom (TM) is also great!). You should check out both of them.
Update #2 – 20131030:
As of this morning, our Palo Alto Firewall at the office is blocking access to the listed Command / Control server for this infection. It is being blocked as a Malware site. The site is still being hosted at linode.com – though I have filed a support ticket to have it taken down. The fact that the server is still operational means that the Command / Control servers are not infection-specific as I had surmised. The registration of the domain was coincidental.
Update – 20131101
I will keep an updated list of Cryptolocker resources from around the Internet here:
- Bleepingcomputer.com – Cryptolocker Ransomware Information Guide and FAQ
- Krebs on Security – How to avoid Cryptolocker randomware